Updated: April 25, 2024
Added new codes!
Recommended Videos
Wealth, fame, and Robux—Gold Roger, the King of the Pirates, gained this and everything else the world offered, and his dying words inspired countless souls to explore the seas: “You want my treasure? You can have it! I left everything I have within Demon Piece codes!”
All Demon Piece Codes List
Demon Piece Codes (Working)
- 1MVISITS—Redeem for a Stat Point Reset (New)
- 25KMEMBERS—Redeem for Double Drops for 15 minutes (New)
- 10KLIKES—Redeem for Double Mastery for 20 minutes (New)
- 5KLIKES: Use for a Stat Point Reset
- 500KVISITS: Use for Double Drops for 15 Minutes
- NEWFIXES: Use for Double Beli for 20 Minutes
- 7KLIKES: Use for Double EXP for 20 minutes
- 750KVISITS: Use for Double Mastery 15 Minutes
- 3KLIKES: Use for x2 Mastery for 10 minutes
- 300KVISITS: Use for x2 Drops for 10 minutes
- SORRYFORLAG: Use for 100,000 Beli
- PERFORMANCEFIX: Use for x2 EXP for 30 minutes
- FOLLOWTWITTER: Use for a Stat Points Reset
- RELEASE: Use for x2 Mastery
- DEMONTIMING: Use for 1,000 Beli
Demon Piece Codes (Expired)
- There are currently no expired Demon Piece codes.
Related: Second Piece Codes
How to Redeem Codes in Demon Piece
To redeem Demon Piece codes, follow our easy guide below:
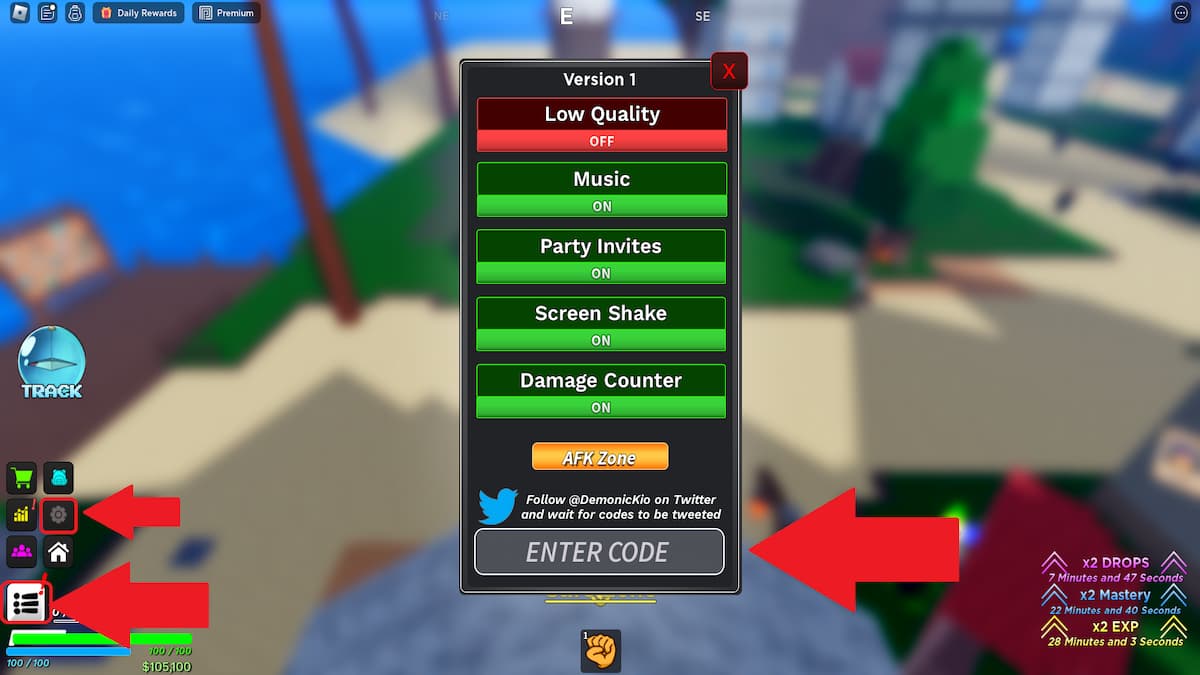
- Open Demon Piece on Roblox.
- Click the menu button in the bottom-left corner.
- Press the cogwheel icon that pops up.
- Enter the code in the ENTER CODE text box.
- Press Enter on your keyboard and receive your freebies!
If you want to play more anime Roblox games with free goodies, check out our Anime Islands Codes and Anime Clash Codes articles, too!
The Escapist is supported by our audience. When you purchase through links on our site, we may earn a small affiliate commission. Learn more





