Updated April 19, 2024
Searched for new codes!
Recommended Videos
Put your helmet on—it’s time for drag racing! Ride some of the coolest bikes in the world and make money while doing so. If you want to get to the top of the leaderboards, you’re going to need the best wheels ASAP—which is where Drag Project codes can help!
All Drag Project Codes List
Drag Project Codes (Working)
- There are currently no working Drag Project codes.
Drag Project Codes (Expired)
- HAPPYNEWYEAR
Related: The Ride Codes
How to Redeem Codes in Drag Project
Redeeming Drag Project codes is a straightforward process—check out our guide below:
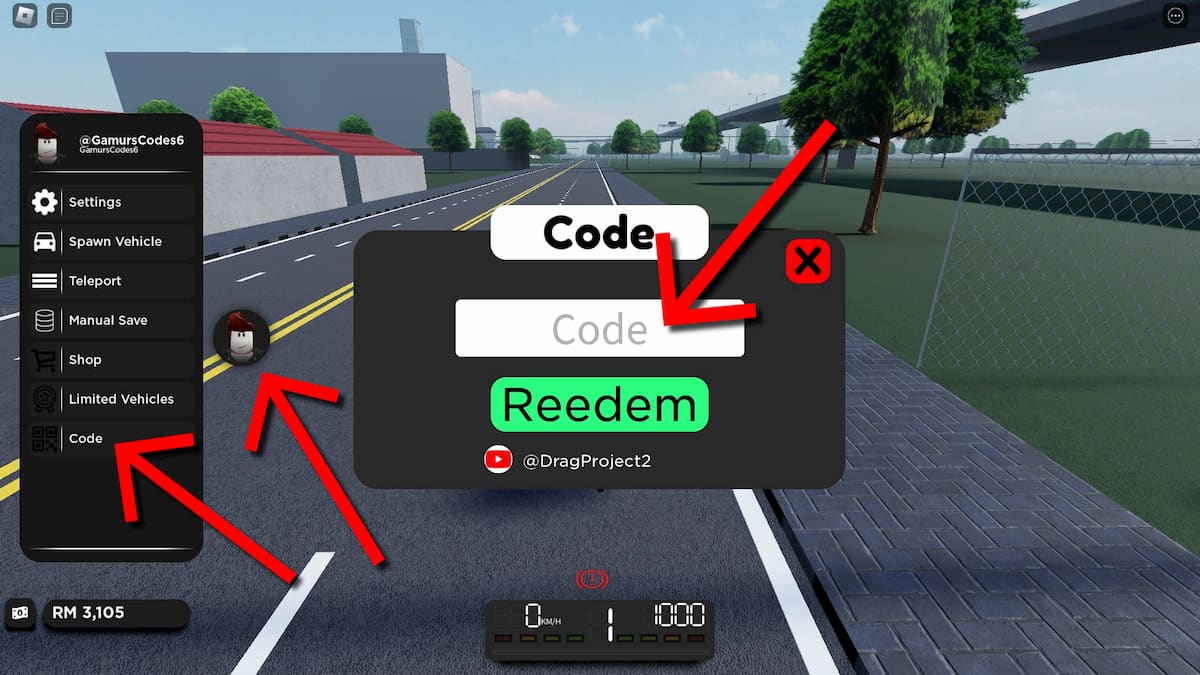
- Run Drag Project in Roblox.
- Click on the player avatar icon on the left.
- Choose Code from the menu.
- Use the Code field to input a working code.
- Click on Redeem to get your free rewards!
If you’re a fan of Roblox games on wheels, check out our articles on MotoRush codes and Car Crushers 2 codes, and grab all the freebies while you still can!
The Escapist is supported by our audience. When you purchase through links on our site, we may earn a small affiliate commission. Learn more





