Updated: May 5, 2024
We added a new code!
Recommended Videos
It’s time to get off the pitch and lock in. What on Earth are you even playing soccer for? If you don’t have what it takes to become the best striker in the world, you won’t survive Blue Lock. However, you might succeed with LOCKED codes.
All LOCKED Codes List
LOCKED Codes (Working)
- 10KGROUPMEMBERS—Redeem for Yen (New)
- QUALITYOFLIFEUPDATE.1—Redeem for Yen (New)
- WATCHTOWER—Redeem for Yen (New)
- 50KFAVOURITES—Redeem for Yen
- 10V10TOURNAMENTBUG—Redeem for Yen
- 25MILVISITS: Use for Yen
- GGRIPTIDE: Use for Yen
- GODSPEED: Use for Yen
- 25KLIKES: Use for Yen
- FROZENTIMER: Use for Yen
- TOURNAMENT: Use for Yen
- TOURNAMENTBUGFIXES: Use for Yen
- 70KMEMBERS: Use for Yen
- NEWCOMMANDS: Use for Yen
- MONSTER: Use for Yen
- DAILYQUESTBUG2: Use for Yen
- SLOTMONEY: Use for Yen
- UPDATE1.5: Use for Yen
- EASTER2024: Use for Yen
- SLOTS: Use for Yen
- PUPPETEER: Use for Yen
- 20MVISITS: Use for Yen
- DELAYEDUPDATE1.5: Use for Yen
- Shutdown0: Use for Yen
- MATCHNAMESHUTDOWN: Use for Yen
- 20KLIKES: Use for Yen
- TASKFIX: Use for Yen
- LOCKEDTINE: Use for Yen
- UPDATE1: Use for Yen
- DELAYNUMBER2: Use for Yen
- DELAY: Use for Yen
- SHUTDOWN6: Use for Yen
- SHUTDOWN5: Use for Yen
- WEAPOBBUGFIX: Use for Yen
- THANKYOUFOR50KMEMBERS: Use for Yen
- VISITS10MIL: Use for Yen
- HALFUPDATE: Use for Yen
- NOOBIE: Use for Yen
- COMMONUNIQUES: Use for Yen
- THANKYOUFOR15KLIKES: Use for Yen
- THANKYOUFOR10KLIKES: Use for Yen
- AFKAREA: Use for Yen
- QUICKFIXED: Use for Yen
- THANKYOUFOR7KLIKES30KMEMBERS: Use for Yen
- HALFUPDATE: Use for Yen
LOCKED Codes (Expired)
- TY2KLIKES
- LIKES3K
- REFUND
- TY1KLIKES
- VISITS500K
- SORRYFORSHUTDOWN
- CONSOLE
- FIELDMAP
- LOCKEDMAS
Related: Anime Souls Simulator X Codes
How to Redeem Codes in LOCKED
To redeem LOCKED codes, follow our easy guide below:
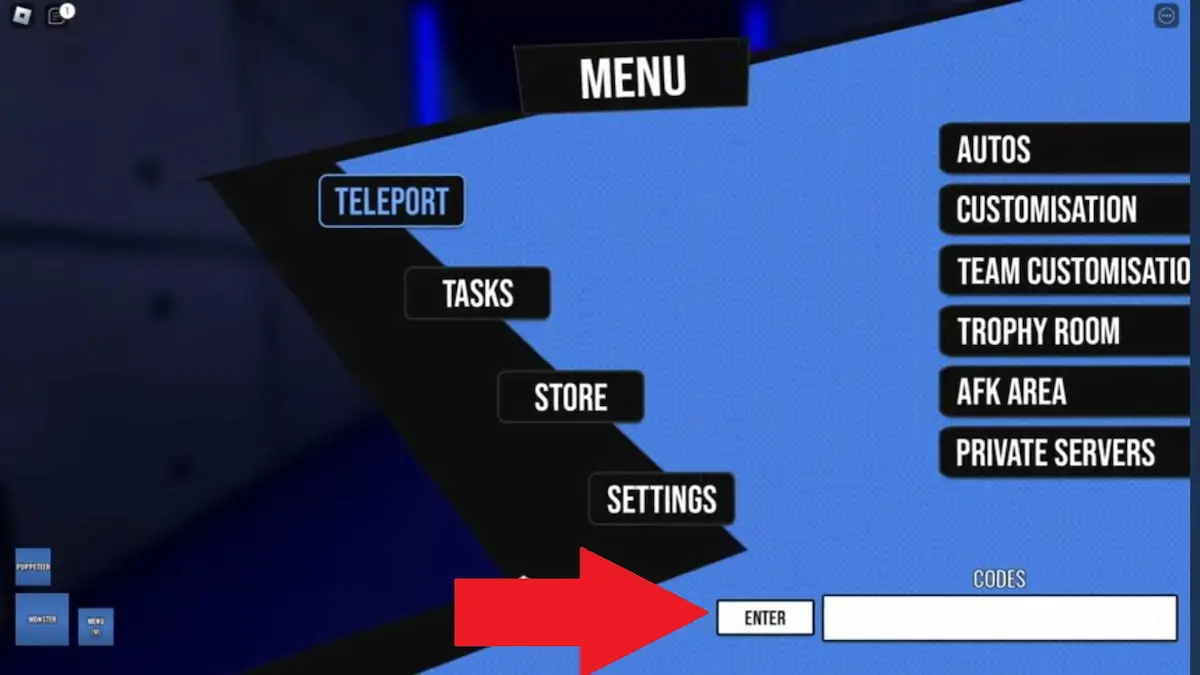
- Open LOCKED on Roblox.
- Press the M key on your keyboard to open the menu.
- Enter the code in the text box in the bottom-right corner.
- Hit ENTER and receive your Yen!
If you want to play more anime Roblox games with freebies, check out our Anime Islands Codes and Anime Clash Codes articles, too!
The Escapist is supported by our audience. When you purchase through links on our site, we may earn a small affiliate commission. Learn more





